Nest Device Access Security Assessment (SDM API)
Comprehensive testing developed in collaboration between Leviathan Security Group and Google to assess and harden the security of any application integrating with the Nest device ecosystem.
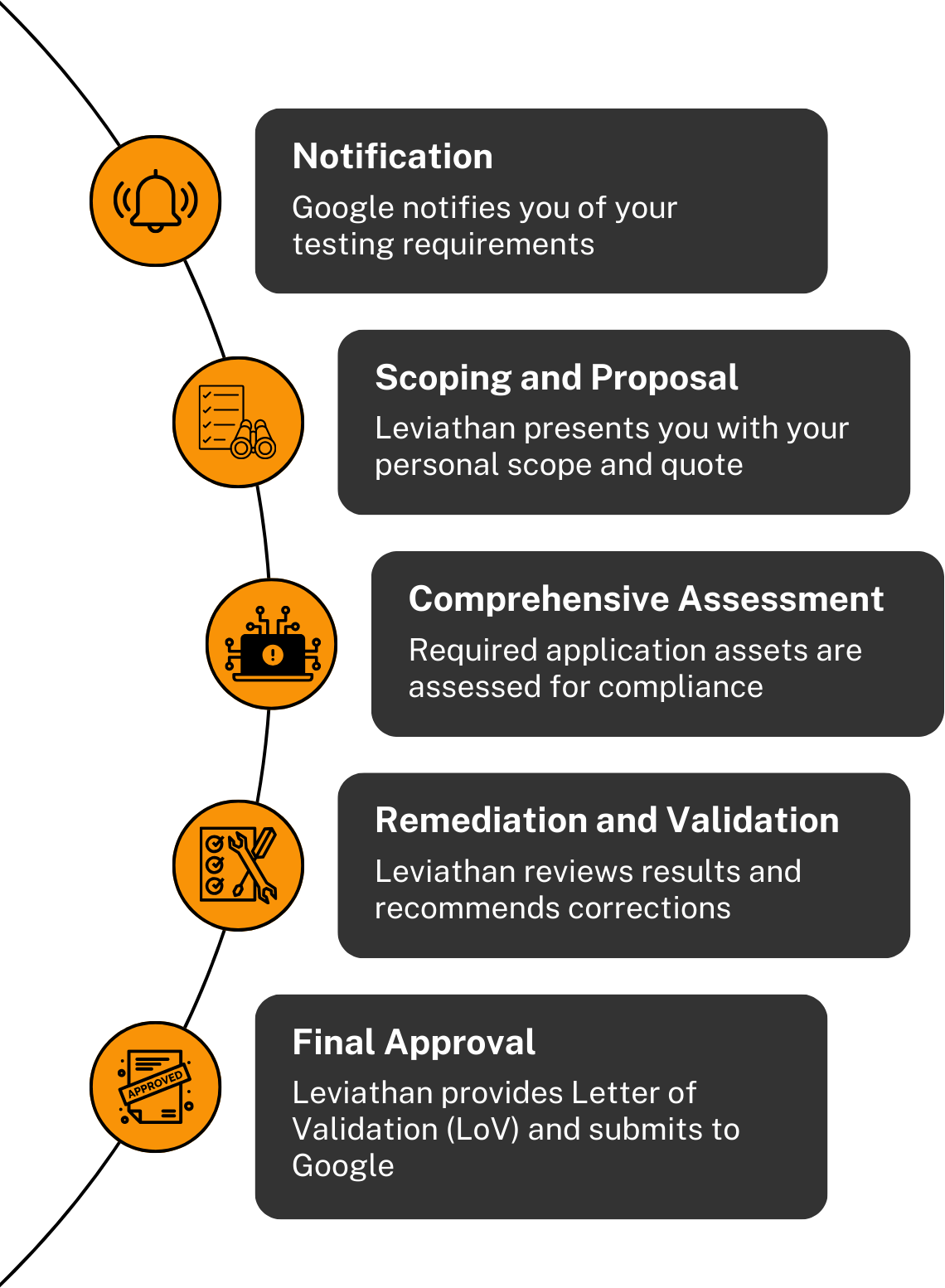
Simplify Your Path to Compliance
Our simplified approach allows us to provide you with a streamlined experience for each application, depending on its unique use case, scale, and complexity.
Offering a white-glove experience to our clients, Leviathan takes care of the pain points involved in the process and delivers clear, transparent, and actionable results.
With Leviathan, you can trust us to handle your application and your assessment process with professionalism and efficiency.
Our Testing Methodology
Our comprehensive testing methodology is designed to identify potential vulnerabilities and ensure that your systems and infrastructure are fully compliant with Google’s requirements for developers integrating with the Nest ecosystem.
Our goal is to provide you with a thorough understanding of your alignment with Google’s expectations and actionable insights to get you where you need to be.
We are committed to maintaining the highest standards of professionalism and diligence in our testing methodology and will support you in any way that we can.
Network Security Testing
We focus on identifying potential vulnerabilities in your external, internet-facing infrastructure. This includes:
Discovery and Enumeration: We identify live hosts, open ports, services, unpatched software, administration interfaces, authentication endpoints lacking MFA, and other external-facing assets.
Automated Vulnerability Scanning and Manual Validation: We use custom tooling to scan for vulnerabilities, followed by manual validation to eliminate false positives.
Brute-Forcing: We test the strength of your security by attempting to bypass authentication endpoints, directory listings, and other external assets.
Vulnerability Assessment: We analyze potential vulnerabilities, insecure configurations, and design flaws to ensure that they are exploitable so we don’t waste your time.
Application Security Testing
We identify potential vulnerabilities in your application to ensure you can find, correct, and resolve any issues keeping you from completing your Nest verification journey:
Real-World Attack Simulation: We simulate real-world attacks to identify and exploit potential vulnerabilities.
Attack Surface Discovery: We discover your application’s attack surface, attempt to bypass authorization, and test for input validation issues.
Dynamic Application Security Testing: We use automated tools to identify potential issues and combine our results with manual validation to identify exploitable vulnerabilities.
Vulnerability Exploitation and Analysis: We exploit software vulnerabilities, insecure configurations, design flaws, and weak authentication in order to provide you with an in-depth analysis of the discoveries made.
User Account Deletion Verification: We verify the ability for users to delete their account with no external indication that the user or user’s content remains accessible.
Deployment Review
We review your developer infrastructure to identify and help you resolve any problem areas to get your application approved swiftly. Our assessment of your developer environment includes:
Configuration Gathering and Analysis
We gather all available configuration settings and metadata to build a profile of the environment. We then analyze this information to identify any gaps or deviations from industry accepted security best practices.
Manual Examination of Configuration Settings
We manually examine configuration settings to locate anomalies and issues such as weak IAM policies, exposed storage containers, poorly defined security groups, insecure cloud services usage, and insecure key management.
Vulnerability Exploitation
When necessary, we exploit vulnerabilities, insecure configurations, design flaws, and weak authentication to demonstrate meaningful impact.
OAuth Token and Key Management Verification
We verify that storage of OAuth tokens is encrypted and that encryption keys and secrets are stored in a hardware security module or equivalent strength key manager.
Developer Access Verification
We ensure that developer access to the deployment environment is secured with multi-factor authentication.
Frequently Asked Questions (FAQs)
How do I know I need a Nest Device Access Security Assessment?
If your app is requesting access to restricted scopes, the OAuth review team will reach out to you when it's time to start the security assessment.
Which OAuth scopes are considered restricted?
Currently, Google considers the following to be “restricted” OAuth scopes with respect to the Nest Device Access program:
SDM API
sdm.service
What applications do not require verification and testing?
If your app is integrating with the SDM API, but is only accessing a user’s thermostat functionality, then you will not need to pursue a security assessment as part of your app’s verification process.
This means that the only authorization scope you are requesting user consent for is the sdm.thermostat.service scope.
How much does it typically cost to complete a Nest Device Access Security Assessment?
This depends and varies between applications. Our team will work with you to develop an accurate scope and quote that is tailored to your application to ensure your application is fully tested and that we don’t charge you more than necessary.
On average, these assessments tend to range between $15,000 and $45,000 depending on various factors such as the size and complexity of the code base, as well as the number of ingress and egress points in your application.
How often does an application need to be verified?
Apps that access restricted scopes are required to complete an assessment every twelve (12) months. The 12-month period is calculated from the effective date of the app’s previous Letter of Validation.
What happens if you discover a vulnerability in an application?
Any high or critical vulnerabilities discovered must be corrected before the final Letter of Validation can be provided. Leviathan will work with you to provide recommendations on how to correct the issues discovered and will validate that the corrections were implemented properly.
What if an app needs to request access to other restricted scopes after receiving a Letter of Validation?
Guidelines recommend the use of production and testing environments to avoid impacting your app’s availability to your customers. Follow these steps when you need to add a new restricted scope to your application:
Add the new scopes to your user consent screen without implementing the new API features in production
Implement the API features in your test environment and request a security validation
Leviathan will work with you to test the features in the test environment and provide a Letter of Validation
Once the Letter of Validation has been accepted, implement the new API features in your production environment